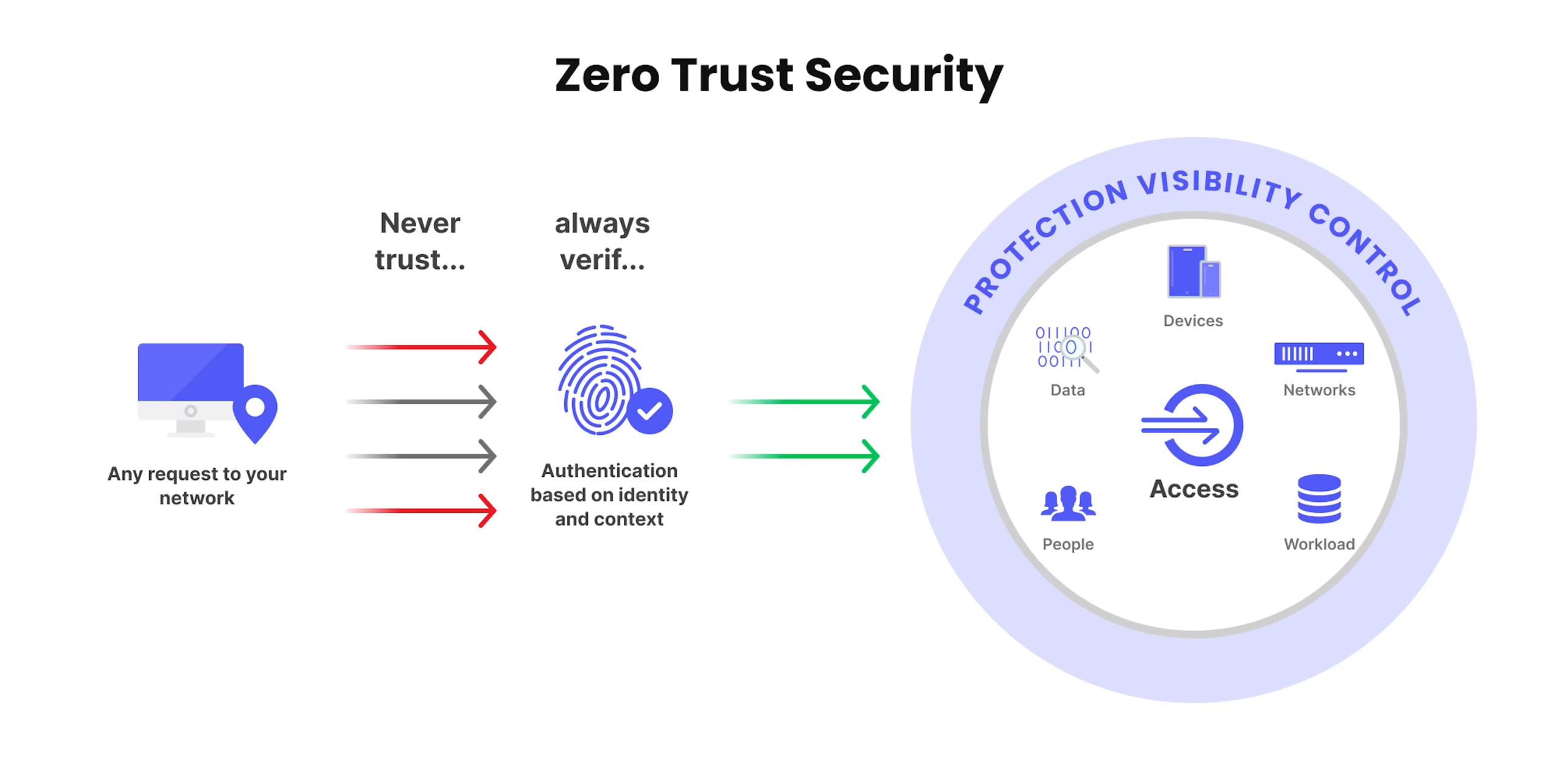
justineanweiler.com – The Internet of Things (IoT) has revolutionized the way we interact with technology, bringing smart devices into our homes, workplaces, and cities. From smart thermostats to connected cars, IoT offers unprecedented convenience and efficiency. However, as the number of connected devices continues to soar, so too does the vulnerability to cyberattacks. This article explores the cybersecurity challenges posed by IoT and discusses potential solutions to safeguard our increasingly interconnected world.
The Growing Threat Landscape
As of 2023, it is estimated that over 15 billion IoT devices are in use worldwide, a number that is expected to triple by the end of the decade. This rapid expansion creates a vast attack surface for cybercriminals. Common vulnerabilities include:
- Insecure Devices: Many IoT devices are built with minimal security features. Default passwords, outdated firmware, and weak encryption make them easy targets.
- Lack of Standardization: The IoT ecosystem lacks universal security standards. Different manufacturers have varying levels of security protocols, leading to inconsistent protection across devices.
- Data Privacy Concerns: IoT devices collect vast amounts of personal data, raising concerns about how that data is stored, shared, and protected. Unauthorized access can lead to identity theft and privacy breaches.
- Network Vulnerabilities: IoT devices often connect to home or corporate networks, creating potential entry points for attackers. A compromised device can serve as a gateway to more critical systems.
Recent Cyber Incidents
High-profile cyberattacks targeting IoT devices have demonstrated the potential consequences of inadequate security. For instance, the 2016 Mirai botnet attack leveraged unsecured IoT devices to launch massive Distributed Denial of Service (DDoS) attacks, affecting major websites and services. Such incidents highlight the urgent need for robust cybersecurity measures.
Strategies for Enhanced Cybersecurity
To mitigate the risks associated with IoT, individuals and organizations can adopt several proactive strategies:
- Strong Authentication Mechanisms: Implementing multi-factor authentication (MFA) can significantly enhance device security. Strong, unique passwords should be used for each device, and default settings should be changed immediately.
- Regular Software Updates: Manufacturers must prioritize the release of security updates and users should enable automatic updates whenever possible to protect against vulnerabilities.
- Network Segmentation: By separating IoT devices from critical networks, organizations can limit the potential damage from a compromised device. Creating a guest network for IoT devices can help safeguard sensitive information.
- Robust Encryption: Ensuring that data transmitted between IoT devices is encrypted can help protect it from interception by unauthorized parties.
- Vendor Accountability: Consumers should seek devices from reputable manufacturers that prioritize security in their products. Advocating for industry standards and regulations can also push manufacturers to adopt better security practices.
- User Education: Raising awareness about IoT security risks and best practices is crucial. Educating users about the importance of security measures can lead to more responsible device usage.
The Role of Legislation and Policy
Governments worldwide are beginning to recognize the importance of IoT cybersecurity. Initiatives like the European Union’s General Data Protection Regulation (GDPR) and the U.S. National Institute of Standards and Technology (NIST) guidelines are steps toward creating a safer IoT landscape. As regulations evolve, they may impose stricter security requirements on IoT manufacturers, fostering a more secure environment for users.
Conclusion
The proliferation of IoT devices presents both opportunities and challenges. While these technologies can enhance our lives, they also create significant cybersecurity risks. By implementing strong security measures, fostering industry accountability, and promoting user education, we can navigate the complexities of IoT in a way that prioritizes safety and security. As we continue to embrace the connected world, vigilance and proactive measures will be essential in protecting ourselves from cyber threats.










Leave a Reply