Decentralized Autonomous Organizations (DAOs), Revolutionizing Governance and Collaboration
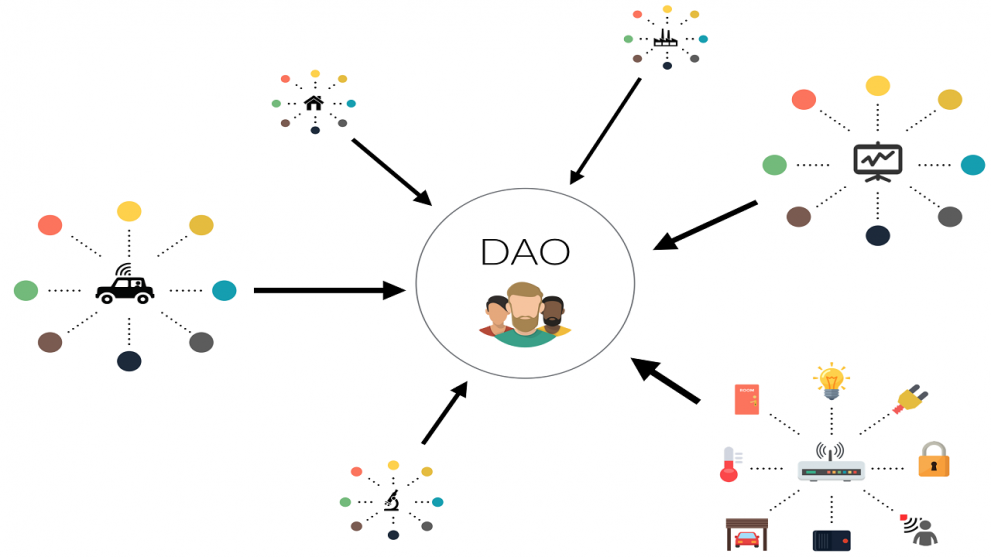
justineanweiler.com – In an era where digital technologies are reshaping traditional industries, Decentralized Autonomous Organizations (DAOs) stand out as a groundbreaking concept that promises to redefine governance, collaboration, and collective decision-making. But what exactly is a DAO, and why is it garnering so much attention? What is a DAO? A DAO, or Decentralized Autonomous Organization,…