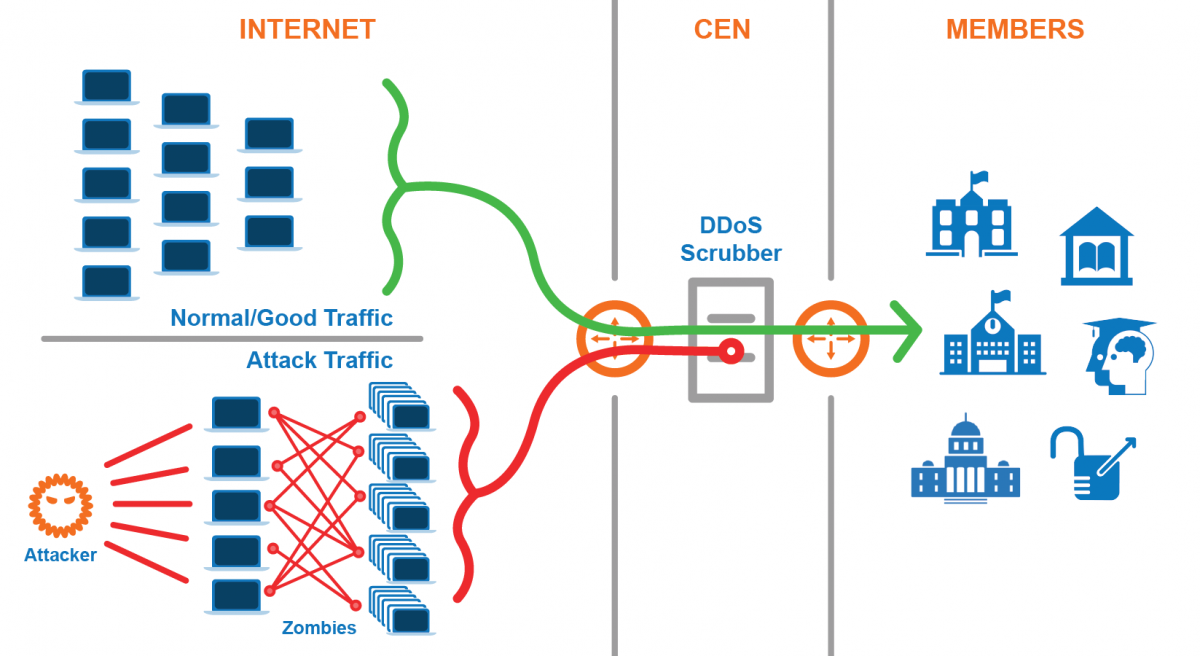
How Blockchain Technology Works
justineanweiler.com – Blockchain technology has become one of the most talked-about innovations of the 21st century, transforming sectors from finance to supply chains, healthcare, and beyond. The concept behind blockchain is rooted in a decentralized, secure, and transparent way of recording transactions, and its applications are vast. Here, we’ll explore how blockchain works, breaking down…