justineanweiler.com – In an era where cyber threats are more sophisticated than ever, traditional security models that rely on a well-defined perimeter are no longer sufficient. Enter Zero Trust Architecture (ZTA) — a modern approach to cybersecurity that challenges the old adage of “trust but verify” and replaces it with “never trust, always verify.”
What is Zero Trust Architecture?
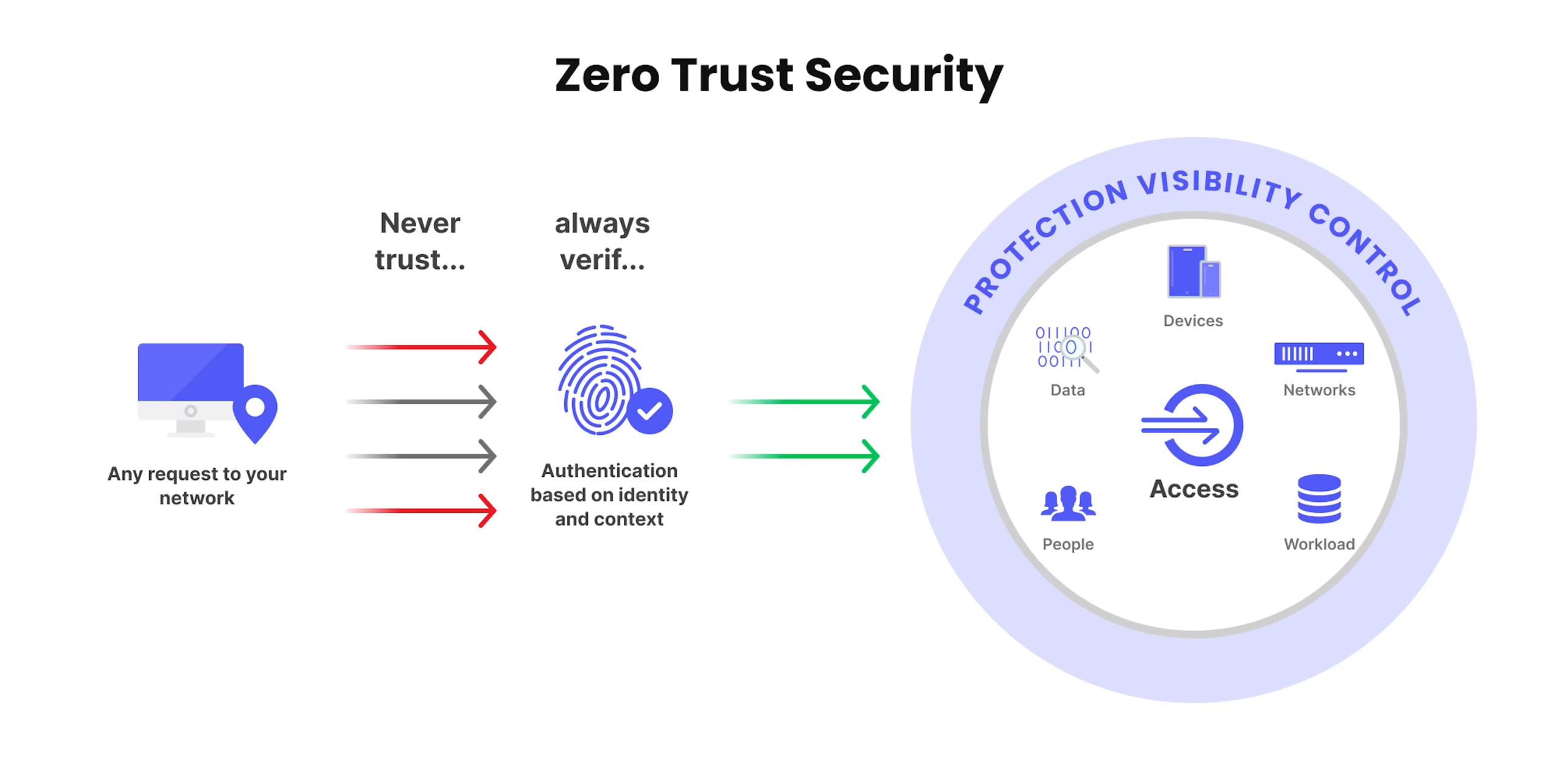
Zero Trust Architecture is a security model based on the principle that no user or system, whether inside or outside the network, should be automatically trusted. Instead, every access request must be verified, regardless of its origin. The goal is to minimize risk by assuming that breaches are inevitable and focusing on limiting their impact.
Core Principles of Zero Trust
- Continuous Verification: Access is granted based on dynamic, context-aware conditions such as user identity, device health, location, and behavior. Verification happens every time access is requested, not just at login.
- Least Privilege Access: Users and devices are granted the minimum level of access necessary to perform their tasks. This minimizes the potential damage in case of a breach.
- Micro-Segmentation: Networks are divided into smaller segments, each with its own security controls. This ensures that even if one segment is compromised, the attacker cannot move laterally across the network.
- Device and Endpoint Security: Continuous monitoring ensures that only secure, compliant devices can access network resources. Compromised devices are automatically denied access.
- Assume Breach: Zero Trust operates under the assumption that threats can come from both inside and outside the network. This mindset drives a proactive approach to threat detection and response.
Key Components of Zero Trust Architecture
- Identity and Access Management (IAM): Robust IAM systems ensure that only authenticated and authorized users can access resources. Multi-factor authentication (MFA) is a critical component.
- Policy Enforcement Point (PEP): The PEP acts as a gatekeeper, enforcing security policies and controlling access to resources based on real-time verification.
- Data Encryption: Data is encrypted both in transit and at rest to protect it from interception or unauthorized access.
- Continuous Monitoring and Analytics: Security teams use advanced analytics and AI-driven tools to monitor user behavior, detect anomalies, and respond to threats in real time.
- Secure Access Service Edge (SASE): A framework that integrates networking and security functions, enabling secure, cloud-delivered access to applications and data.
Benefits of Zero Trust Architecture
- Enhanced Security: By verifying every access request and limiting access to resources, ZTA reduces the attack surface and minimizes the risk of data breaches.
- Improved Compliance: Zero Trust helps organizations meet regulatory requirements by providing detailed access controls and audit trails.
- Adaptability: The model supports modern, decentralized IT environments, including cloud computing, remote work, and IoT devices.
- Reduced Insider Threats: By assuming that no user or device is inherently trustworthy, ZTA mitigates risks posed by malicious or compromised insiders.
Challenges in Implementing Zero Trust
- Complexity: Transitioning to Zero Trust requires significant changes to existing infrastructure and processes.
- Cost: Implementing ZTA can be resource-intensive, requiring investment in new tools, training, and expertise.
- Cultural Resistance: Organizations may face pushback from employees or teams who perceive Zero Trust policies as overly restrictive or disruptive.
- Integration Issues: Ensuring that all legacy systems and third-party applications align with Zero Trust principles can be challenging.
Steps to Adopt Zero Trust Architecture
- Assess Current Security Posture: Conduct a thorough evaluation of your existing infrastructure, identifying gaps and vulnerabilities.
- Define a Zero Trust Strategy: Develop a roadmap that outlines objectives, priorities, and a phased approach to implementation.
- Implement Identity-Centric Controls: Strengthen IAM systems, including MFA and role-based access controls.
- Segment the Network: Use micro-segmentation to isolate critical assets and apply granular access controls.
- Monitor and Adapt: Continuously monitor network activity, analyze threat intelligence, and refine policies based on evolving risks.
The Future of Zero Trust
As cyber threats continue to evolve, Zero Trust Architecture is expected to become the standard for securing digital environments. Advances in AI, machine learning, and automation will further enhance its effectiveness, enabling organizations to stay ahead of attackers.
By adopting Zero Trust, organizations can build a robust, adaptive security framework that not only protects critical assets but also fosters trust in an increasingly interconnected world.