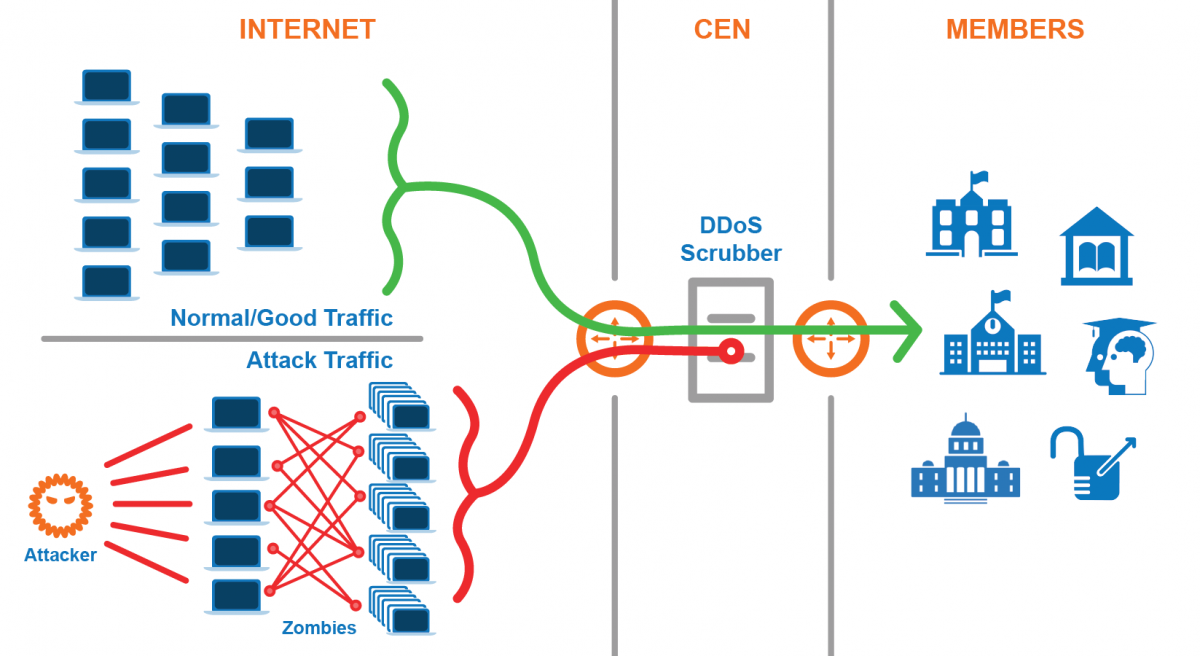
justineanweiler – Distributed Denial of Service (DDoS) attacks are a malicious attempt to disrupt the normal functioning of a targeted server, service, or network by overwhelming it with a flood of internet traffic. Unlike traditional Denial of Service (DoS) attacks, which typically come from a single source, DDoS attacks originate from multiple compromised computers, often part of a botnet. This makes them more challenging to mitigate and defend against.
Types of DDoS Attacks
- Volume-Based Attacks: These attacks aim to consume bandwidth and include methods like ICMP floods and UDP floods.
- Protocol Attacks: These target the network layer and include SYN floods and Ping of Death attacks, which exploit weaknesses in protocols.
- Application Layer Attacks: These focus on specific applications and services, such as HTTP floods, aiming to crash web servers by overwhelming them with requests.
The Impact of DDoS Attacks
DDoS attacks can lead to severe consequences, including:
- Downtime: Businesses may experience service interruptions, resulting in lost revenue.
- Reputation Damage: Frequent downtimes can harm a company’s reputation and customer trust.
- Increased Operational Costs: Organizations may incur costs related to incident response and recovery.
Mitigation Strategies
While it’s impossible to eliminate the risk of DDoS attacks completely, several strategies can help organizations mitigate their effects:
- Use a Content Delivery Network (CDN): CDNs can absorb traffic spikes and distribute the load across multiple servers, reducing the strain on the main server.
- Implement Rate Limiting: This strategy involves limiting the number of requests a server will accept from a single IP address within a specified timeframe, helping to prevent overwhelming traffic.
- Deploy DDoS Protection Services: Many providers specialize in DDoS mitigation and can offer real-time monitoring and filtering of malicious traffic.
- Maintain Redundant Infrastructure: Having multiple servers and data centers can help distribute traffic and reduce the impact of an attack.
- Configure Firewalls and Routers: Properly configured firewalls can block unwanted traffic. Implementing rules to filter out known malicious IP addresses is essential.
- Establish an Incident Response Plan: Organizations should have a well-defined plan in place to respond quickly to a DDoS attack, including communication strategies and recovery processes.
- Regularly Update and Patch Systems: Keeping systems and software up to date can help prevent attackers from exploiting known vulnerabilities.
- Monitor Traffic Patterns: Implementing monitoring tools can help identify unusual traffic patterns indicative of a DDoS attack, allowing for quicker response.
Conclusion
DDoS attacks pose a significant threat to organizations of all sizes. By understanding the nature of these attacks and implementing effective mitigation strategies, businesses can better protect themselves against potential disruptions. Continuous vigilance and preparedness are essential in the ever-evolving landscape of cybersecurity.









Leave a Reply