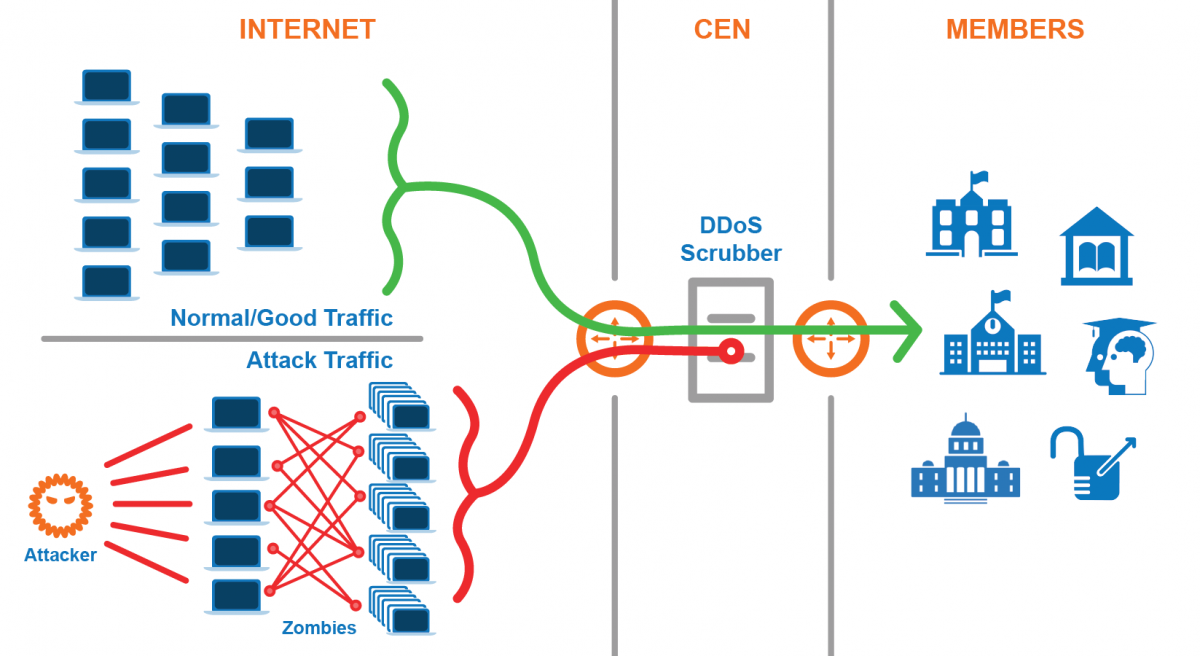
Will We Have Retina ID on Mobile Phones in the Future?
justineanweiler.com – As mobile phone technology continues to evolve, biometric security features like fingerprint scanners and facial recognition have become standard. But what about Retina ID—the idea of using a person’s retina to unlock their phone? While this technology hasn’t become mainstream yet, there is a strong possibility that Retina ID could be a key…