How Coding Works?
justineanweiler.com - In today's digital age, coding is everywhere—from the apps on your smartphone to…
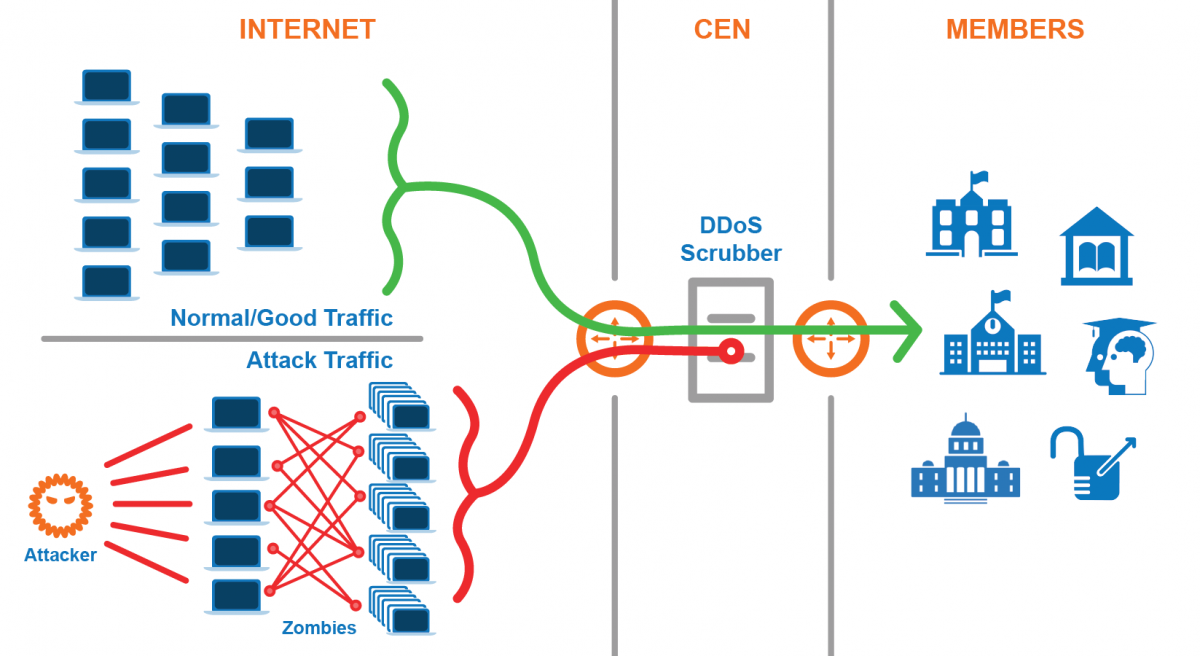
How to Avoid a Cyber Attack?
justineanweiler.com - In today’s highly connected digital world, cyber attacks are becoming more frequent and…
Smartwatches and Fitness Trackers
justineanweiler0 - In recent years, smartwatches and fitness trackers have transformed the way we monitor…
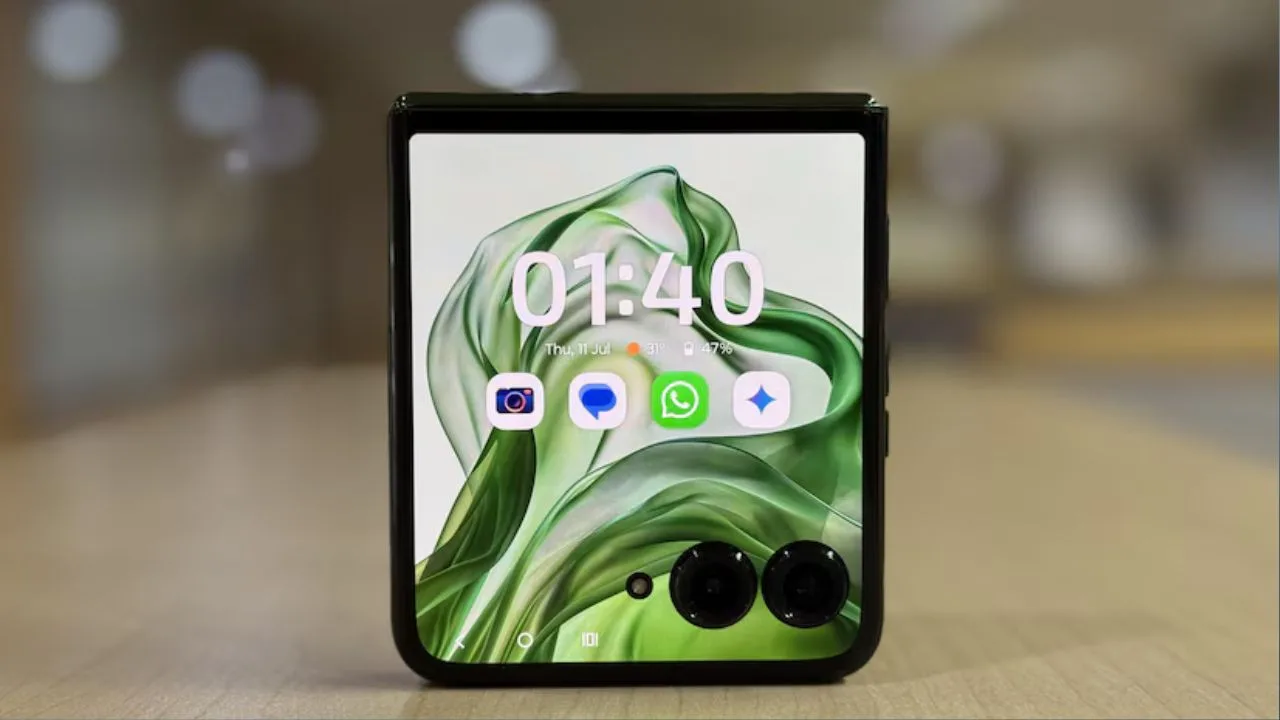
Motorola Razr 50 Ultra: Reviews and Impressions
justineanweiler.com - The Motorola Razr 50 Ultra is Motorola’s latest flagship foldable phone, and it’s…
The Evolution of Social Media Platforms
justineanweiler - Social media has transformed the way we communicate, share information, and connect with…
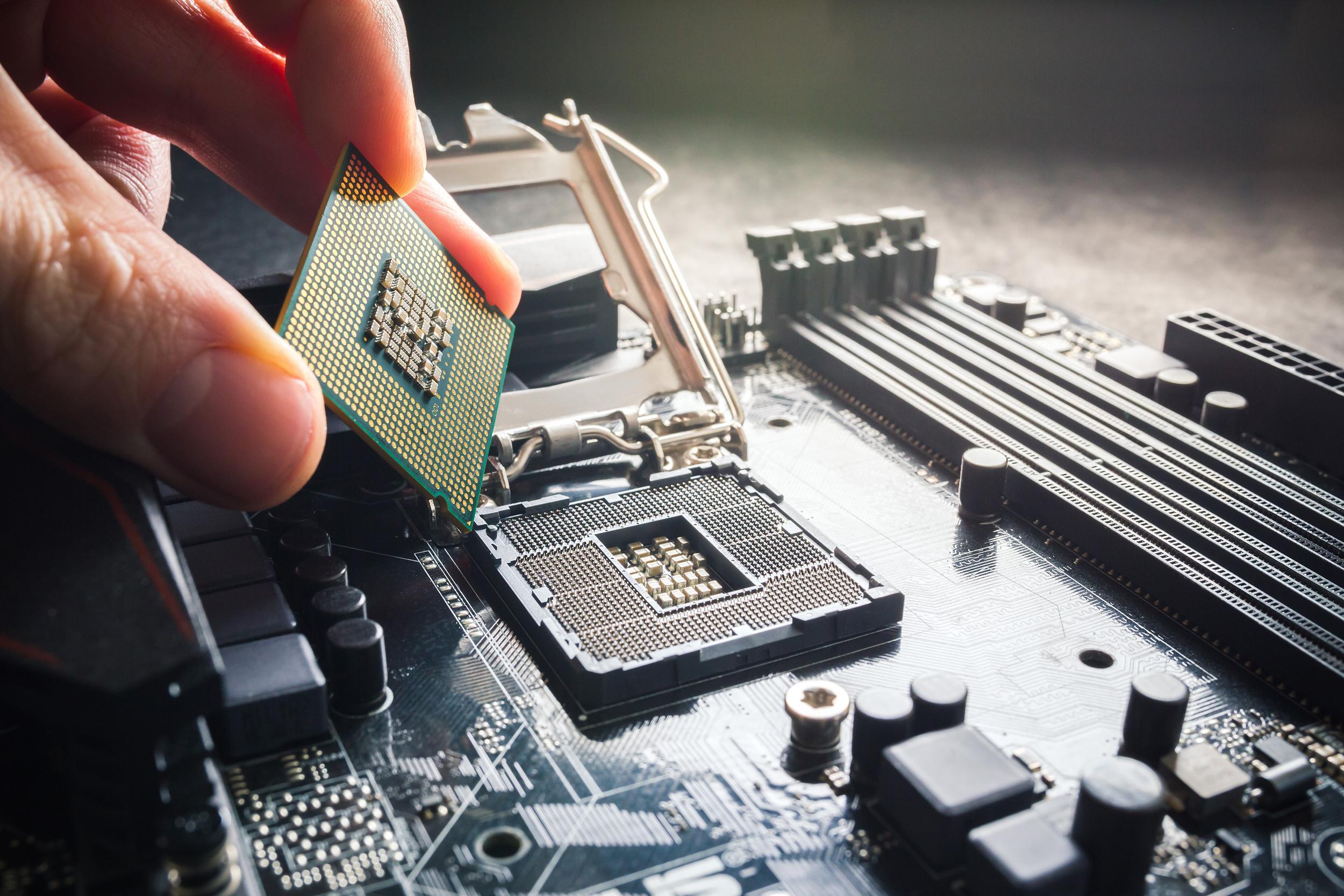
How a Computer Processor Works
justineanweiler.com - The computer processor, often referred to as the central processing unit (CPU), is…
Why the iPhone’s Processor Is So Fast and Optimal
justineanweiler.com - Apple’s iPhone processors, known as the A-series chips, are renowned for their speed,…
The Evolution of Cloud Computing, Transforming the Digital Landscape
justineanweiler.com - Cloud computing has revolutionized the way businesses operate, enabling them to access technology…
Malware-as-a-Service, A Growing Business for Hackers – Darktrace Report
justineanweiler.com - Malware-as-a-Service (MaaS) has become a booming underground business, enabling anyone, even those with…